Several tools have come up in the market for stopping cyber crimes and attacks. Network IDS helps in preventing unwanted data from entering into the network system. The intrusion detection system is an application for inspecting a network and giving alerts for authorized entries into the network system. IDS software focuses on internal network trafficking for identifying any kind of suspicious activity. It allows IDS for detecting all kinds of attacks originating directly from the network.
IDS network comes with certain solutions using combinations of signature-based detection for comparing traffic. This is normally done for databases having known attacks or techniques. They are continuously looking for the detection of suspicious activities varying differently in the organization.
1. The need for establishing Network IDS
Using Firewall does not give protection for long as hackers and attackers are always searching for new techniques in entering a network system. Many attackers try leveraging other software for the creation of credentials granting access to specific data in the network. Many types of IDS help detect and determine malicious traffic. The main reason behind using network ids is ensuring an IT professional about any attack taking place in the company. IDS software looks after all kinds of data traversing whether inbound or outbound
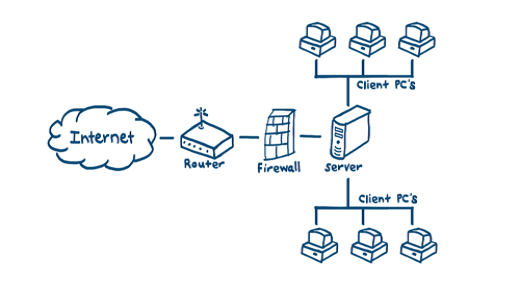
Between all systems of the network. It monitors the network in any suspicious activity. In this way, IT professionals examine the problem closely and help by taking appropriate steps in blocking the same.
2. Actions on IDS network alerts
There are many types of IDS and using it effectively is the key to getting free from cybercrimes in the organization. While trying to search for any kind of traffic in the network, there can be both false positives and negatives in any malicious activities. Its professionals should take decisions based on the alert they are receiving. The two types of network ids are listed as under:
False positives
False positives are mostly found while doing anomaly-based detection and identification of attacks and crimes. False-positive is one such situation of considering normal activity as a threat without knowing the main reasons behind it. IT professionals make this mistake with IDS software by not knowing the difference between normal and legitimate activities. They do not allow the right traffic to come to the network.
False Negative
Then there comes the part of false negatives. In this segment, you will be able to detect malicious activity through an IDS network not detected 100% accurate at all times. This is mostly seen with zero days or also with new kinds of emerging threats. It attacks all those networks and uses IDS techniques not very familiar with the IDS network.
3. Having security experts
Network IDS also faces other challenges like having new alerts every single time. The only way of stopping this is by seeing that you have professional and qualified IT professionals for weeding out all the unnecessary alerts. They should focus on identifying threats missed out by IDS software. Attacks can happen any time without any kind of timing for that. Your company must have a Security Operation Centre with professionals for checking all threats and alerts all the time.
4. Some benefits of network IDS
Made specific contents with network packages
Many people prefer using Firewalls for protecting their network and it has been able to function properly. But with network ids, you will get to know of all the specific contents coming within the packets. It helps in uncovering intrusions like exploitation attacks acting part of the network IDS.
Boosting efficiency
IDS software has sensors for detecting devices and hosts and inspecting data within the range of network packets. They also identify places utilizing the network. IDS save a lot of time rather than following the same process manually. Network IDS also works towards automating hardware inventories thus saving labor work. All of these help in boosting the efficiency of the organization by reducing the cost of staff and the onset cost reduction takes place.
Quantifying of attacks
Network IDS helps in identifying the number of attacks in a company. This helps in changing any information to better technology of using new controlling systems effectively. Analyzing bugs and network configuration problems become easy. Attacks are quantified saving time for future assessments as well.
Detecting threats and preventing the same is an important task in all organizations and should be done with the same amount of enthusiasm as with other works. Employing experts for the same saves employees time for doing all other work.
Related Resources: