IDS Security
In this digital era, networks are a part of our life. They are a boon to the world. They bring the world closer to us. With the network, the threat of intrusion became very common. The virtual world is never free from hackers. Your organization might be vulnerable to cyber-attacks.
So, what is IDS in security? No firewall is reliable, nor are networks inaccessible. Hackers continuously develop new techniques to attack the system. An Intrusion Detection System (IDS) is a tool that recognizes an attack on the network. It takes immediate steps to evaluate such activities and restore them to normal. Thus, IDS in security is crucial in your network. It will help you to detect traffic. IDS will immediately send an alarm. This will help the IT team to take steps for such issues.
But it won't prevent an attack from settling systems. It estimates daily operations against the baseline. An alert is sent to the security operation center. Thus, it becomes easy for the security specialist to detect such suspicious tasks.
The traffic data is transferred together and then evaluated for any suspicious activities in the data. ISD investigates attacks based on familiar attack signatures and patterns.
TYPES OF IDS TOOLS
- Host-Based Intrusion Detection System
- Network-Based Intrusion Detection System
How do intrusion detection systems work?
We must be thinking about how it functions. The answer is very simple.
IDS are a technology that discovers anomalies that catch hackers before they do real harm to our network. They can network or host-based. A host-based intrusion detection system is fixed on the client computer. A network-based intrusion detection system inhabits the network.
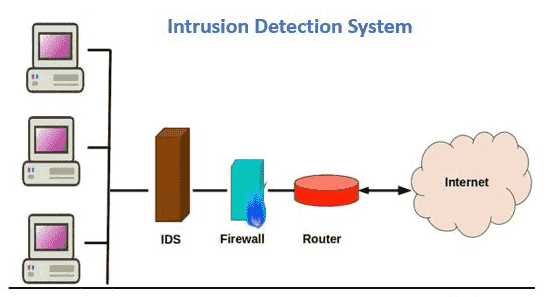
IDS look for signatures from known attacks from the normal task. These anomalies are raised to the stack and then evaluated at the protocol and application layer. IDS may be used either as a software application or as a network security appliance.
Functions of the Intrusion Detection system in the network security
Following are the functions of IDS, which make it popular among its various clients—
- It keeps an eye on the functions of routers, firewalls, key management servers, and files.
- It provides continuous support to the users.
- Arranges the various audit trails and other logs.
- It generates an alarm when security breaches are detected.
- Once the suspicious activity is detected, they block the server immediately.
Advantages of Intrusion Detection Systems
The intrusion detection system provides a wide range of benefits to an organization.
It keeps a check on all the incoming and outgoing network activity. It detects any signs of intrusion in the system. Its main function is to send an alert immediately when it identifies any activity in the system.
It recognizes various security incidents. Also helps to examine the quantity and types of such suspicious attacks. It also detects bugs and issues relating to their network device configurations. An organization can use this information and fix the problem. They may change their security system or take some effective measures.
IDS sensors identify hosts and other network devices. They tend to examine the data within the network and the operating system. This saves the time of the IT team. Thus, the efficiency of the organization increases. This will help the organization to cut off the staff cost.
IDS can also be used as a tool to meet certain requirements. They offer transparency across your network. Thus, it helps the organization to meet with different regulations for security.
Challenges of Intrusion Detection Systems
Everything comes with pros and cons. IDS comes with a certain curse that needs to be known.
At times they might send some false alarms. Thus, an organization needs to detect such things when they are first using it. They need to configure the system so that they can easily identify normal traffic. They can easily distinguish any malicious activity.
Such false alarms sometimes can create some serious issues. IDS might skip a threat to such recognized traffic. In such a scenario, the IT teams have no sign that an attack might take place. Thus, they will fail to take any steps. Thus, it is advisable to be careful about such abnormal behaviors.
IDS help to monitor the network. But they don't block or resolve such issues. The organization needs to hire the right personnel to look after such threats and take immediate action.
Intrusion Detection Systems are suffering from a serious issue. They fail to detect a new suspected intrusion, as the new malware does not display the pattern of previous unusual behavior. Thus, the IDS must take steps to detect such new behavior. So that an organization can take immediate precautions to such a threat.
Related Resources: