Securebox Application Containerization Technology
Using Secure Application Containerization Technology Stop app data theft by shielding the application
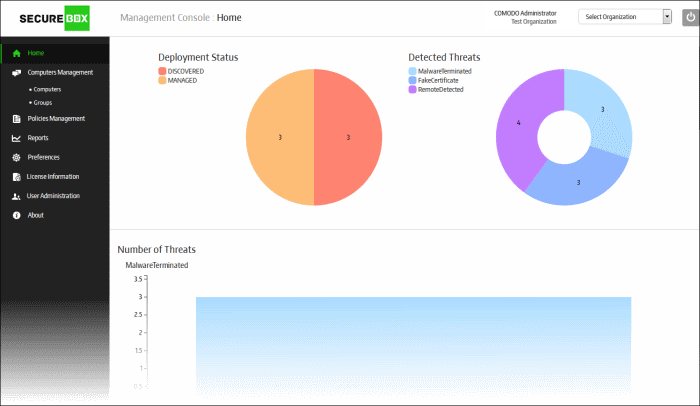
INSTANT BUSINESS BENEFITS OF SECURE APPLICATION CENTRALIZATION
Comodo’s sophisticated verdicting engine provides you insight with 100% trust on all files in your network at lightning speed

Protection Against All Attack Vectors

Customizable Protected Applications

Control Critical Applications Remotely

Protect Any Point-of-Sale Devices
Wrap the classified data inside a security-hardened environment
KEEP YOUR APPLICATIONS SAFE USING SECURE APPLICATION CENTRALIZATION
Malicious emails are everywhere and pose as legitimate communication from coworkers and connections, luring users to click. With a Zero Trust architecture, businesses can prevent damage from malicious emails. Comodo’s Secure Email Gateway never trusts and always verifies 100% of unknown files, providing businesses with bulletproof email security and an uninterrupted user experience.
Protect against 100% of unknown email executables, while still allowing users to immediately run unknown files
Prevent email-spoofing and impostors that target your organization’s sensitive information
Quick and easy deploy customizable policies and advanced search options with all major MTAs compatible
Spam is more than an annoyance; it’s a costly productivity-killer. Large volumes of unwanted emails overflow inboxes, hiding legitimate emails. Comodo’s Secure Email Gateway uses a sophisticated array of spam filters, anti-virus scanners, phishing prevention and content analysis engines to prevent unsolicited mail from ever entering the network.
-
Protect against 100% of unknown email threats,
without user interruption. - Prevent users from leaking sensitive data through email.
- Block spam before it even enters the network
Security needs differ from employee to employee. Apply security profiles and permissions for various departments and users to protect sensitive data within the organization.
-
Create user-based profiles to apply different levels of
security for different departments and roles. -
Perform advanced searches to locate
important information quickly. -
Easily access any emails in the archive,
without losing any past emails.
WHY CHOOSE OUR
SECURE APPLICATION CONTAINERIZATION
Secure sensitive data from exposure by email by creating user-based policies, enabling advanced
threat protection, and preventing email data leakage with Comodo’s Secure Email Gateway.
Protection against keylogger software
Prevent kernel-level drivers to be intercepted
Halt hackers eavesdropping your connection
Fault internet attacks that bypass SSL/PKI
Records of your typing cannot be stolen
Hackers won't be able to disable your security
Stops memory of sensitive data to be stolen
Intruders cannot download malicious files
Save time by remotely using offsite equipment
Signature updates live in your dashboard
Analyst Recognition
![]()
![]()
![]()
![]()
![]()
We’ve won consecutively across many verticals with our premier technology. Innovation happens only when this type of dedication to cybersecurity reaches the many
Quickly identify threats lurking on your network with 100% file verdicts in under 5 minutes