What is Website Security?
Website security refers to maintaining the security of websites, web servers and web applications.
A website is always prone to malware attacks. Hence website security includes scanning websites, servers and applications for malware and vulnerabilities, and includes timely detection and prevention of threats and vulnerabilities including malware threats, zero-day vulnerabilities, DDoS attacks, brute-force attacks etc. The focus is on data protection and includes sensitive personal data of customers as well.
What is Comodo cWatch?
Comodo cWatch Web is a Managed Security Service (MSS) operating in a Security-as-a-Service (SaaS) model. This means it is software (no appliance required) designed to protect your company's web activity. The web is a small businesses' principal venue for its IT operations and increasingly so for businesses of all sizes.
cWatch Web software runs on Comodo's high capacity cloud – the Content Delivery Network (CDN) to host the protection / detection software at geographically placed servers around the globe. There are many security delivery advantages to this architecture - ease of deployment and agility in its upkeep to an ever-changing threat – and some that come by default, such as DDoS mitigation and greatly accelerating your website traffic.
Supporting the security software and supporting you is also a professional team, deep in expertise and deep in strength supporting the services on a 24/7 basis for every day of the year. cWatch Web is the active – always on security patrol for the critical operation that is the website in e-commerce, branding, reputation, routing customers to your business.
Benefits of Comodo cWatch
- Reduced Cost - we manage your entire monitoring and security incident investigation process, for on-premises, cloud, or hybrid environments. You can avoid the costly investment of hiring and training an internal security team.
- Managed security, delivered as-a-service - with our Software-as-a-Service (SaaS) solution, there isn't any complex implementation or maintenance–just the latest security technology and Global Information Assurance Certification (GIAC)-certified analysts working for you.
- Security expertise for a swift recovery - improve your overall security posture and recover from breaches and compromises faster with dedicated help from security experts.
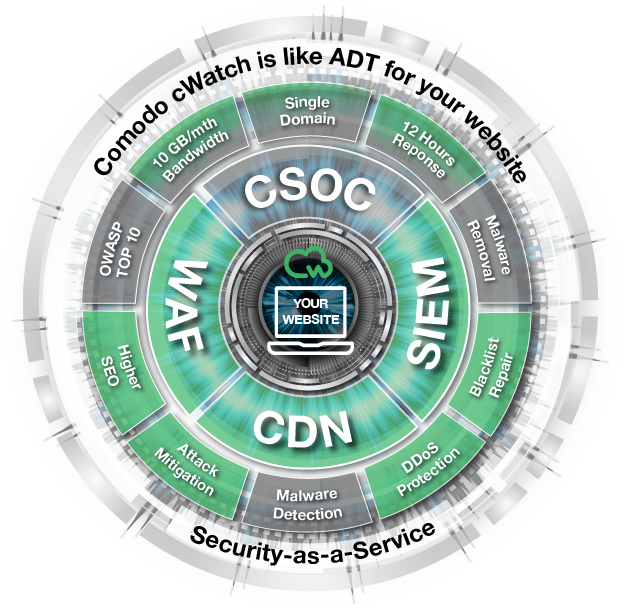
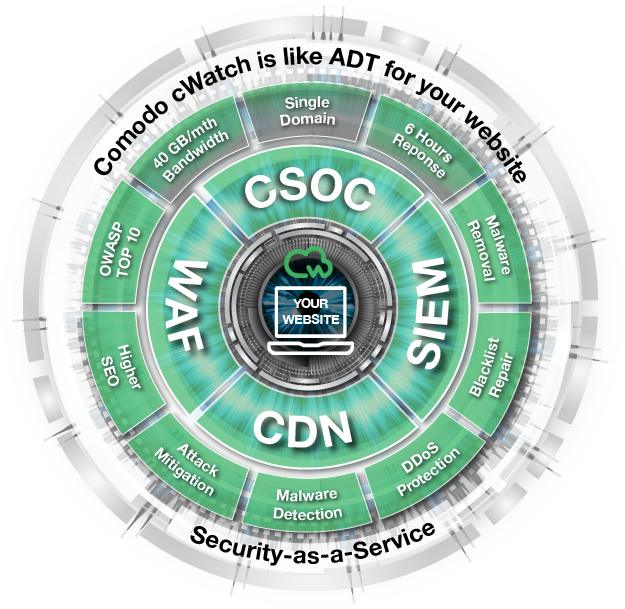
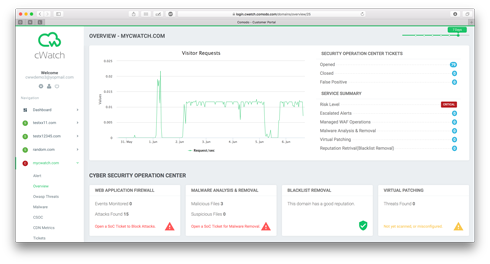
Comodo cWatch Website Security Platform
Starting with the intent to provide the most robust client website security possible – the way the web works to counter the many threats that exist - Comodo engaged its engineers to meet this challenge and deliver the solution at a price point that works starting even for the smallest business. This is cWatch Web. It is our website security platform serving as host to a bundle of integrated web security features. Navigate through the different tabs to learn more – the details that describe how it works and how we met the challenge.

Pro
| CDN Site Boost | 200/Gbps |
| Lvl 1 Support | 24 / 7 / 365 |
| Web App Firewall |  |
| Unlimited Malware Removal |  |
| Auto Site Scanning |  |
| Virtual Patching |  |
| Expert Security Tuning |  |
Premium
| CDN Site Boost | 500/Gbps |
| Lvl 1 Support | 24 / 7 / 365 |
| Web App Firewall |  |
| Unlimited Malware Removal |  |
| Auto Site Scanning |  |
| Virtual Patching |  |
| Expert Security Tuning |  |
Partner Program Designed For Every Partner Type
-

Hosting Provider
Increase average customer value by bundling managed security with your dedicated, shared, or cloud hosting solutions.
-

Security Specialist
Extend your security offering with capabilities with managed security solutions.
-

Managed Solutions Provider
Add website security to the managed services you provide to expand your reach and value to your customers.
-

E-Business Partners
Differentiate yourself from the competition. Drive higher conversions with solutions that can be implemented in just a few clicks.
Contact Us to learn if Comodo cWatch Web is right for your customers.
Why Partner with Comodo?
Secure your customers website and applications. Extend your revenue potential. Develop long-term customers.
-
cWatch Web is In Demand
Businesses of all sizes are turning to managed security services to help them stay ahead of the ever-evolving cyber threat landscape.
-

Revenue Potential
Comodo offers generous margins and incentives for partners to grow their business with us to go along with a monthly reoccurring revenue model.
-

Support
Our partners are at the heart of our business. We provide best-in-class 24x7 pre and post sales support globally.
-

Sales & Marketing Tools
Leading sales & digital marketing tools to drive demand, acquire new customers and increase average revenue per customer. We create marketing programs with partners for all stages of the sales cycle.
-

People
The Comodo partner team has the most combined knowledge and experience in the industry . Partners receive a dedicated team that is committed to a successful partnership.
Get Started with the Comodo Partner Program
Ready to get started? Or, just want to learn more about the Comodo Partner Program or cWatch Web?
Complete the form to get started.
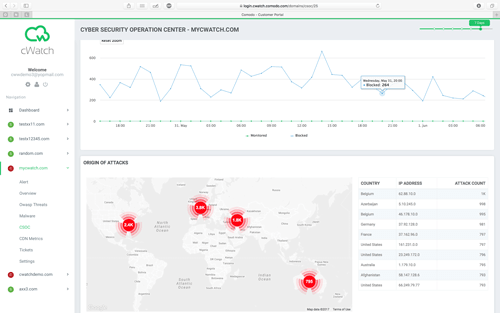
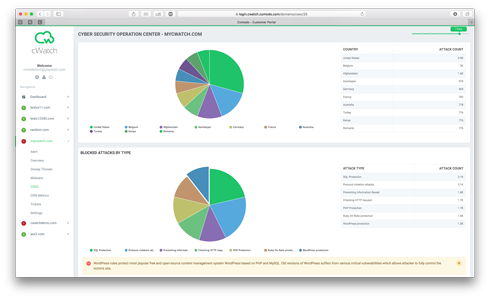
What is Comodo Cyber Security Operations Center (CSOC)?
The CSOC provides 24/7 security monitoring by certified security analysts and using state-of-the-art technology. Analysts at the CSOC identify and analyze threats, provide alerting when appropriate to engage clients in resolution and to assist in mitigation.
Comodo cWatch CSOC extends your internal IT team's capacity to protect your applications with advanced security solutions that are easy to implement, fully managed and do not require large upfront investments. It is designed to absorb the time-consuming and complex security incident investigation process, while offloading the high costs of an in-house security staff.
With real-time web traffic monitoring and proactive incident identification, our security experts are able to notify organizations and take necessary actions quickly when an attack is detected.

Benefits of CSOC
- Continuous monitoring by Comodo CSOC security experts that have deep expertise in application security monitoring and management
- Real-time security event monitoring
- 24/7 incident handling and response
- Expert tuning and configuration management
- Continuous policy and prevention updates
- Continuous web application firewall management
- Complete threat investigations and analysis
- Threat assessment reports to identify risks
- Reverse malware and suspect application engineering
- Security expertise for a swift recovery
A sophisticated response to increasingly complex cyber attacks
With our dependence on the web to conduct business and other types of transactions, there has been an alarming rise in attacks with some that have gained international notoriety. The ransomware attack called WannaCry launched in 2017 was just the latest in a string of attacks that grow bolder with greater consequence. The reasons for this rise are many including attempts to obtain technical, financial, strategic, and national security data from governments, private industry, our critical infrastructure providers, as well as private citizens. This kind of threat requires protections equal to the task - assertive measures to detect, respond, and quickly adapt to new cyber threats that may jeopardize security.
Comodo's twenty years of cyber security innovation using methods to determine provenance – a fancy word that means the history of ownership to determine trust. The ability to make this determination underlie the speed of decisions to detect malware code, to block malicious websites and determine whether a file or application can be trusted. The CSOC analyst supported services are part of the cWatch web offering using a variety of sources, intelligence gathering, threat detection, incident response, digital forensics, and security monitoring. Entrusted to protect networks with the most at stake, Comodo is now applying its CSOC best practices to help customers stay ahead of the ever-evolving cyber threat.

Security Information and Event Management (SIEM)
SIEMs are expensive tools with equally expensive integration consulting costs to get the tool into operation with the right logs – tuned to a client's specific environment. And they suffer other issues like agility – able to change with the rate and sophistication of modern day threats. Comodo's cWatch SIEM is owned by Comodo and the client user interface is free – bundled with the service in the SaaS model. There is no training required as it is entirely designed for an intuitive ease of use. Set up is instantaneous - no additional cost. At operation, it has the SIEM-typical reporting features of other competitors but the simplicity for ease of use is a key feature: simple information and event management to tackle real-time security monitoring, advanced threat detection, forensics and incident management. With an analytics-driven SIEM, Fully Managed WAF and Comodo's industry leading Cyber Security Operation Center (CSOC) in the background. cWatch Web builds the awareness that is essential to understand the cyber-state-of-protection of your web presence.
The SIEM is essentially the brain of the Cyber Security Stack – sitting at the top of the WAF, CDN malware detection and compliance reporting protections.
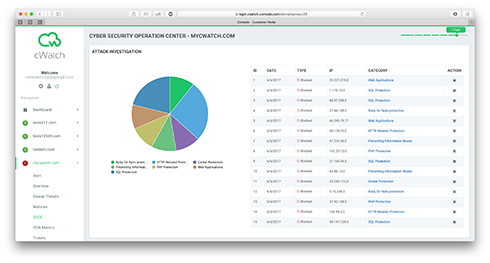
Provides real-time visibility
- Scans and detects malware embedded in applications used to commit a large variety of different attack escalations. Successful attacks that reach the point of impact require a series of steps to gain entry, hide, and negotiate the next step that can include privilege escalation, communicating to an external command and control site - all to the end purpose of achieving the attacker's objective. cWatch Web disrupts the attacker's process so the malicious impact is stopped well before any damage is done.
- The WAF rules / signatures are updated in the SIEM
- Obtains information from the vulnerability scans - web and application vulnerability scanners.
- Reduces and prioritizes alerts
- Performs immediate event normalization and correlation for threat detection and compliance reporting.
- Reduces billions of events and flows into a handful of actionable offenses and prioritizes them according to business impact therein empowering Comodo's CSOC with actionable intelligence
- Enables more effective threat management
- Senses and tracks significant incidents and threats, providing links to all supporting data and context for easier investigation.
- Performs event and flow data searches in both real-time streaming mode or on a historical basis to enhance investigations.
What is an Information Security event?
A security event is a change in the everyday operations of a network or information technology service indicating that a security policy may have been violated or a security safeguard may have failed.
SIEM software products and services combine security information management (SIM) and security event management (SEM). They provide real-time analysis of security alerts generated by hardware and applications.

Benefits of Comodo's analytics driven SIEM
Provides real-time visibility
- Visibility: Enhance incident response and investigations using security and non-security data collected across your organization.
- Context: Collect, aggregate, de-duplicate, and prioritize threat intelligence from multiple sources to enhance your security investigations.
- Efficiency: Streamline security operations by conducting rapid investigations using ad-hoc searches as well as static, dynamic and visual correlations to determine malicious activities.
- A Big Data Platform: Using a modern, big data platform enables you to scale and solve a wide range of security uses cases for CSOC, Security Operations and compliance.
- Ease of Deployment: cWatch Web deployment requires a re-pointing of the website CNAME to complete the registration process. There is no hardware or additional steps needed to complete the process.
- Behavioral Analytics: Combines Big Data Analytics with Machine Learning techniques to produce actionable intelligence of known and unknown risks and is tuned to detect zero day threats, optimizes Security Operations and reduce complexity, speeding up the ability to investigate and respond to threats and attacks.
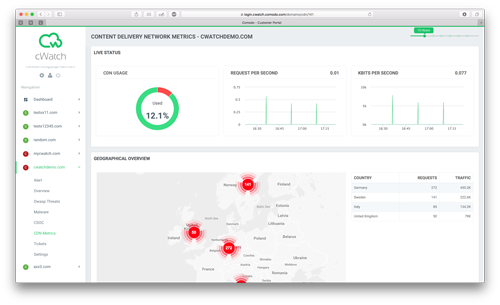
What is a Content Delivery Network (CDN)?
A CDN is a system of distributed servers (network) that deliver web pages and other web content to a user based on the geographic locations of the user, the origin of the web page and a content delivery server.

Benefits of a CDN
- Faster Speeds: by creating a copy of your website data at over 29 locations around the world, your data will no longer need to travel great distances to reach your customer. A person from Europe will load your data from a CDN node in Europe, even If your website is hosted on a server in the USA. Shorter distance = faster speed.
- High Availability: since the CDN will be serving your content, with virtually unlimited capacity, you have the freedom to scale up & down with your traffic needs, automatically. Large, even unexpected surges in traffic (like when a blog post goes viral) will no longer bring your server to a crawl, allowing you to keep your site operation under critical conditions.
- SEO Rewards: search engines, such as Google, reward sites using CDN. Websites that are faster in general rank higher in results increase traffic and get your website noticed by utilizing CDN technology.
- Save Money: larger files take longer to transfer than smaller files. When your data is compressed, it takes up less space and can therefore reach your customer much quicker. Many CDNs support compression and allow one to also leverage browser caching technology (so your users don't download the same content more than once). Smaller files = less bandwidth used = money saved.
- Content Protection: a neat feature of CDN is that you can protect content with a few settings tweaks. If you are looking to protect “premium/paid” content, or simply prevent hot-linking, you can put in place flexible key and Proxy authentication.
- Security: Comodo is the only web services platform built on security, with a fortified, machine learning core that aggregates, analyzes and syndicates real-time threat data both to and from each of our secure services. With Comodo, security is what's built on, not bolted on.
Comodo's Secure CDN Features
The most secure CDN in the world - fully integrated with Security Information and Event Management (SIEM and Web Application Firewall (WAF)
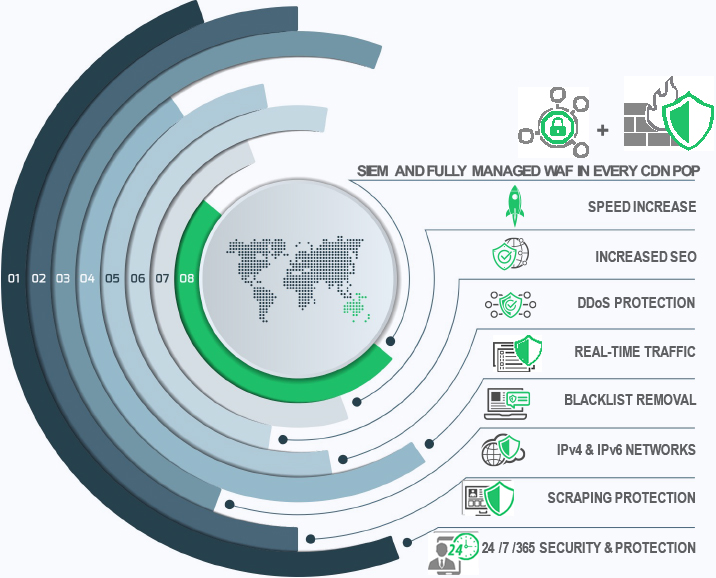
Comodo's Secure Content Delivery Network
- Developer Friendly (Advanced settings for fine control, and automation via RESTful API)
- Low Latency (Geo-distributed DDoS protection is installed in all Points of Presence (PoP), meaning no geographic increase in latency)
- Layer 7 Protection (op layer firewall for threat detection, mitigation and syndication)
- Dynamic Filtering (Behavioral and reputational filtering of threat data automatically and in real-time)
- Static Rules (User definitions such as IP address, HTTP header content, country, and session ID)
- Integrated WAF and SIEM in each PoP (Comodo cWatch Web is the most secure CDN in the world)
Integrated WAF and SIEM in each Point of Presence (PoP) make Comodo cWatch the most secure CDN in the world
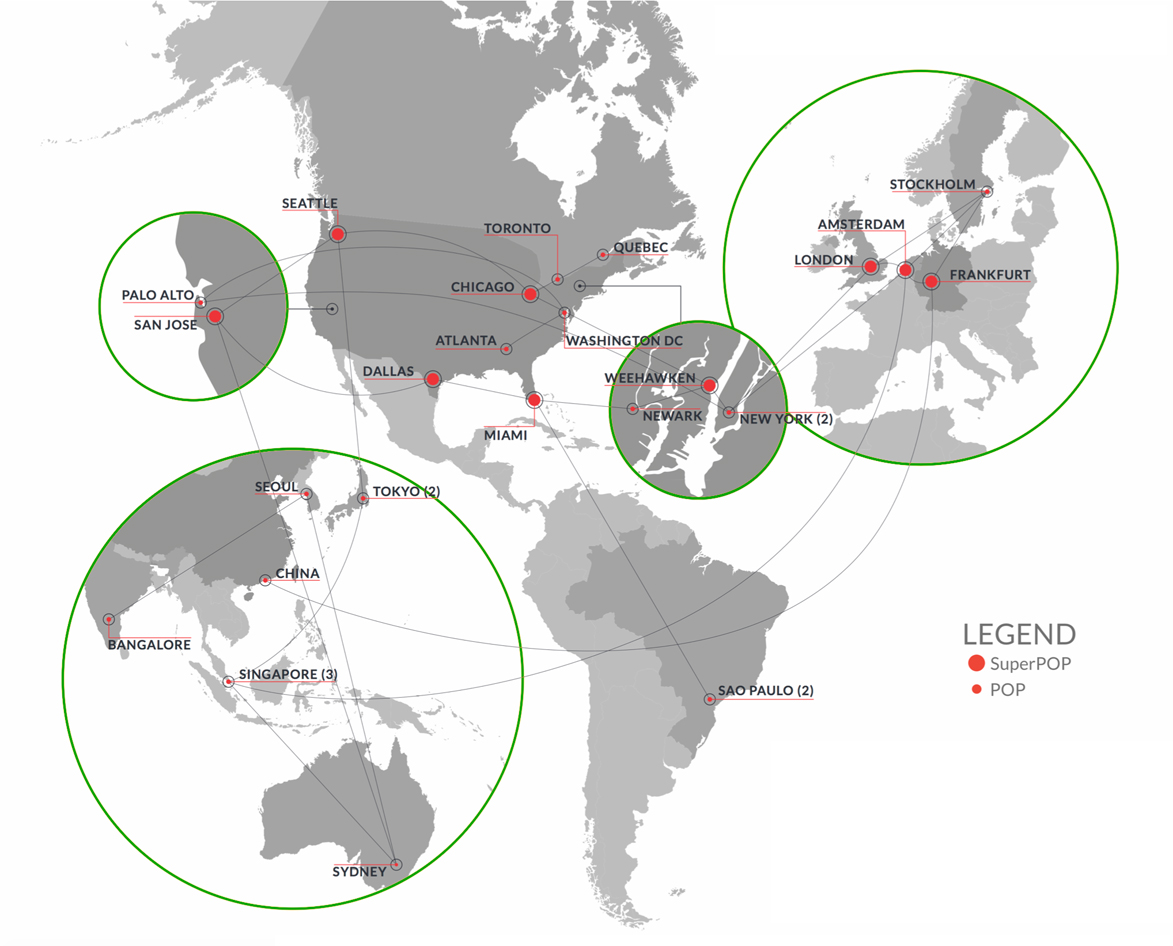

Quick Facts
- 28 Points of Presence (PoP)
- 28 PoP with fully integrated Comodo cWatch SIEM and WAF
- 15 Information Exchange (IX) Memberships
- 100 Gigabit Ethernet (100G) uplinks
- 1400+ unique Internet Protocol version 4 (IPv4) and IPv6 Border Gateway Protocol (BGP) Neighbors
What is WAF (Web Application Firewall)?
A WAF is an online security solution that analyzes, blocks, or filters out bad traffic between a client and a web application.
Comodo's Fully Managed Web Application Firewall
The Comodo Fully Managed Web Application Firewall is an innovative cloud-based Website Application Firewall (WAF) and Intrusion Prevention System (IPS) for protecting websites. It functions as a reverse proxy by intercepting and inspecting all incoming HTTP/HTTPS requests to your website and stripping them of any malicious requests before the they arrive safely at your server. Comodo's WAF is fully managed meaning that we provide the updates to keep it current with automatic virtual patching and hardening engines that offer real-time mitigation of threats, with no impact to the website.
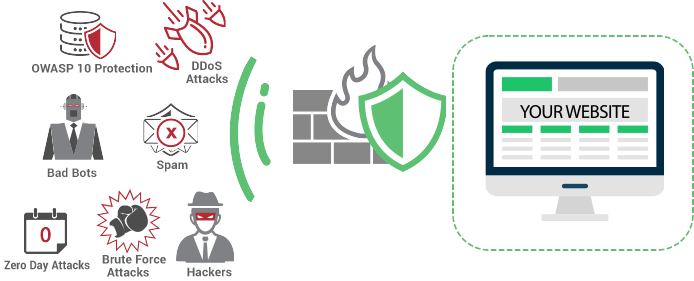
Protects your website from hackers, DDoS Attacks and many many more
Malicious Bot and Brute Force Prevention
Malicious bots and brute force attacks are blocked from your your websites. Protection of account registration forms and login pages from various attack vectors
- Throttling of Access Attempts to Entry Points
- Malicious Bot Detection and elimination
- Protect from application denial of service, reconnaissance attacks and web scraping.
Zero Day Immediate Response
Zero Day attacks relate to an undisclosed vulnerability that is exploited by someone with the purpose of achieving an impact before there is an available mitigation / patch. Zero day attacks against web servers and the web application (your website) are of great concern for the absence of a remediation but an equally vexing concern is when patches are not applied for known vulnerabilities. Comodo's cWatch Web services address both these concerns, first by the regular update of virtual patches for all websites under management and second by the immediate response to apply a patch for the zero day attacks when they become known to the public. These capabilities are listed below as
- Virtual Hardening
- Virtual Patching
- Protection in the Cloud
Stop Website Attacks and Hacks
The biggest contributing factor to website hacks comes from insecure code – software that fails to follow secure coding techniques and fails to test the software using commonly available tools that check for vulnerabilities. Attackers are always looking for new weaknesses (zero day attacks) to exploit. The Comodo Firewall protects vulnerable websites by identifying and removing malicious requests and hack attempts. Our constant research allows the Comodo Firewall to thwart emerging exploits.
- SQL Injection Attacks
- Cross Site Scripting (XSS)
- Threat Intelligence
- Web Application Vulnerabilities
- Application Targeting Attacks: Joomla, WordPress and plugins, Drupal etc.
Distributed Denial of Service Protection
Comodo's approach to mitigating network-based attacks includes investing in resources across all Points of Presence (PoP). The globally-distributed Anycast network enables efficient distribution of traffic. It explicitly blocks all non-HTTP/HTTPS-based traffic, with a current network capacity in excess of 1 TB/s. Each PoP has multiple 10G and 100G ports, designed to scale and absorb very large attacks.
- Layer 7 HTTP Flood Attacks
- DNS Amplification Attacks
- SSDP Attacks
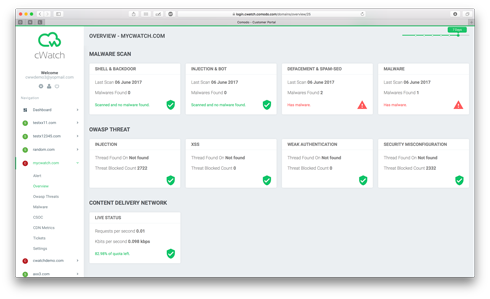
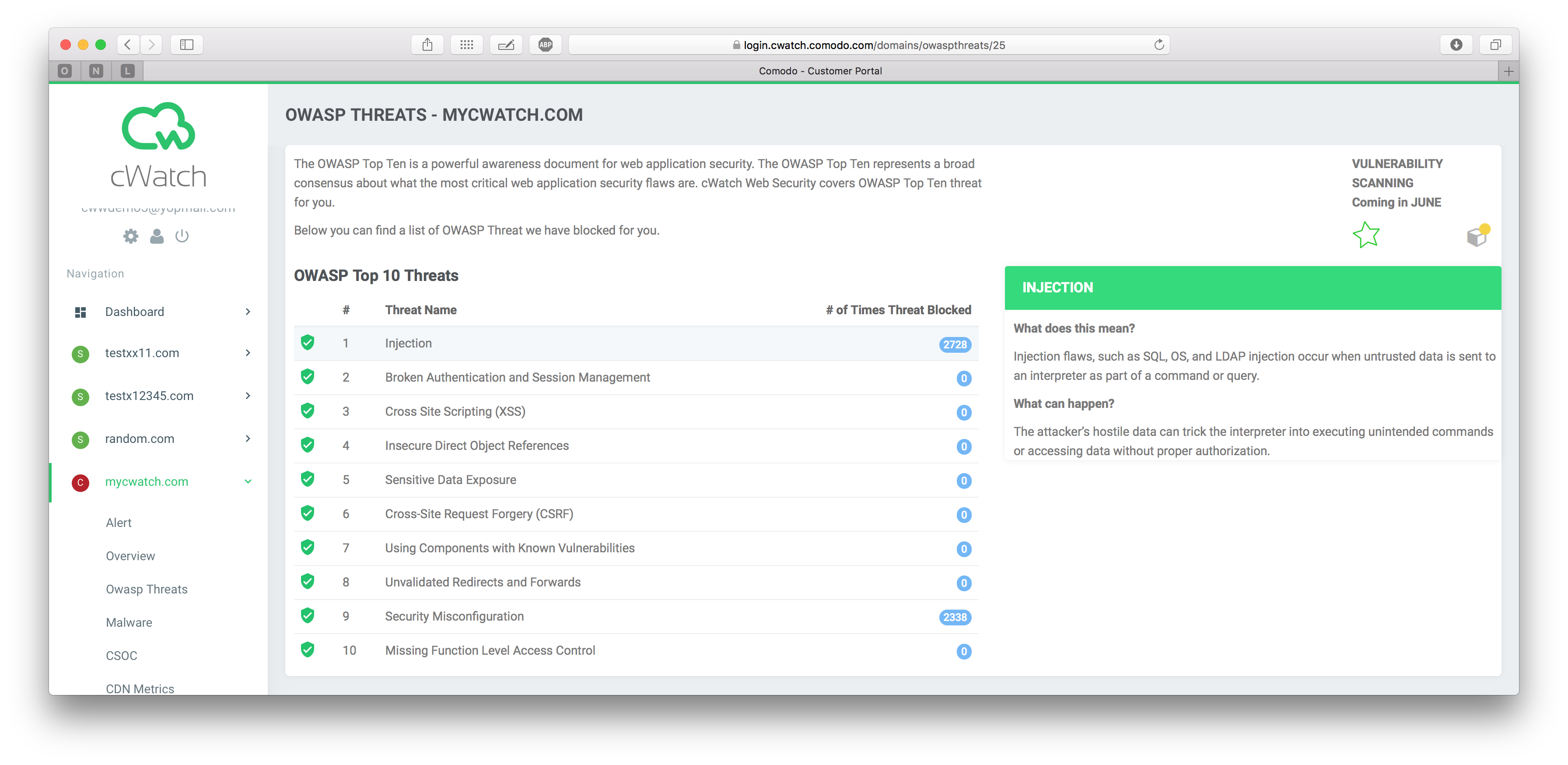
The OWASP Top 10
The Open Web Application Security Project (OWASP) Top Ten is a published list of the top ten forms of website attacks determined by polling experts in web communication to achieve a broad consensus on what threats should be of greatest concern. This list is helpful to industry to focus the mitigation attention. Comodo cWatch covers OWASP Top 10 and provides an easy way for you to see which categories you pass or fail.
-

SQL Injection
Injection flaws, such as SQL, OS, and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker's hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
-

Security Misconfiguration
Good security requires having a secure configuration defined and deployed for the application, frameworks, application server, web server, database server, and platform. Secure settings should be defined, implemented, and maintained, as defaults are often insecure. Additionally, software should be kept up to date.
-

Cross Site Scripting
XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim's browser which can hijack user sessions, deface websites, or redirect the user to malicious sites.
-

Insecure Direct Object References
A direct object reference occurs when a developer exposes a reference to an internal implementation object, such as a file, directory, or database key. Without an access control check or other protection, attackers can manipulate these references to access unauthorized data.
Comodo cWatch Protects against OWASP Top 10
-

Sensitive Data Exposure
Many web applications do not properly protect sensitive data, such as credit cards, tax IDs, and authentication credentials. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data deserves extra protection such as encryption at rest or in transit, as well as special precautions when exchanged with the browser.
-

Broken Authentication & Session Management
Application functions related to authentication and session management are often not implemented correctly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users' identities.
-

Missing Function Level Access Control
Most web applications verify function level access rights before making that functionality visible in the UI. However, applications need to perform the same access control checks on the server when each function is accessed. If requests are not verified, attackers will be able to forge requests in order to access functionality without proper authorization.
-

Cross Site Request Forgery (CSRF)
A CSRF attack forces a logged-on victim's browser to send a forged HTTP request, including the victim's session cookie and any other automatically included authentication information, to a vulnerable web application. This allows the attacker to force the victim's browser to generate requests the vulnerable application thinks are legitimate requests from the victim.
-
Components with known vulnerabilities
Components, such as libraries, frameworks, and other software modules, almost always run with full privileges. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications using components with known vulnerabilities may undermine application defenses and enable a range of possible attacks and impacts.
-

Un-validated redirects & Forwards
Web applications frequently redirect and forward users to other pages and websites, and use untrusted data to determine the destination pages. Without proper validation, attackers can redirect victims to phishing or malware sites, or use forwards to access unauthorized pages.
Frequently Asked Questions (FAQ)
How do I sign up for Comodo cWatch Web Security?
Click here to sign up for Comodo cWatch Web Security or click here to start a 30 day free trial.
Where do I login to Comodo cWatch Web Security?
Click here to login and Comodo cWatch Web Security and enter email address and password used to sign up as username and password.
How do I upgrade my license?
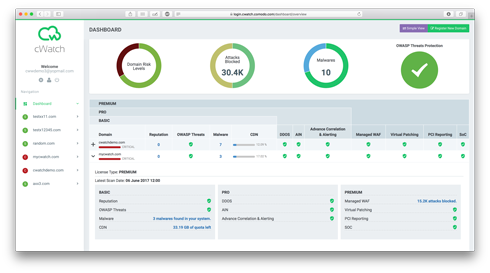
To upgrade your license:
1) Login to the Comodo cWatch Web Security
2) Click on Dashboard in the Navigation
3) Select License to upgrade
4) Confirm upgrade by clicking Yes
5) See License upgraded successfully pop up
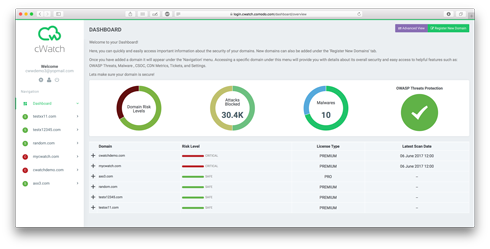
How do I register a new domain?
To register a new domain:
1) Login to the Comodo cWatch Web Security
2) Click Register New Domain
3) Enter Domain Name excluding www
4) Select License from License to use for the domain that is going to be registered
5) Click Register and Next
6) The remaining steps are optional; however you need to configure your domain to make it protected.
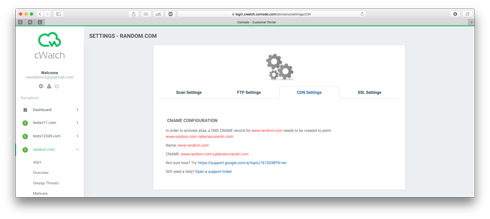
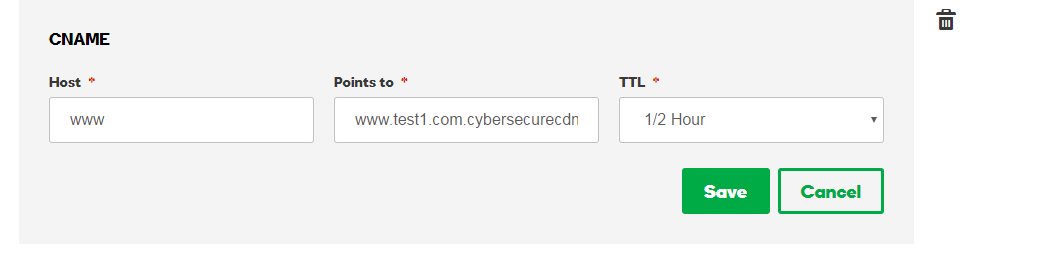
How do I configure CDN / DNS - CNAME?
To configure CDN / DNS - CNAME:
1) Login to the Comodo cWatch Web Security
2) Click Register New Domain
3) Click domain name on left menu
4) Click Settings
5) Click CDN Settings
6) Copy the CNAME given, for example www.test1.com.cybersecurecdn.com
7) Add CNAME to your DNS settings (click here for more information about adding a CNAME record)
Sample Configuration on GoDaddy (On Hosting)
8) Make request to your site (On Hosting)
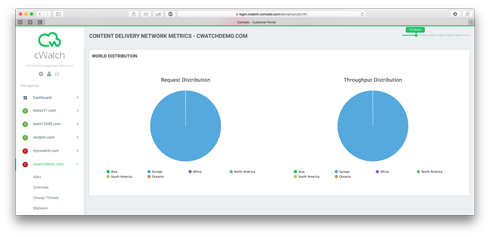
9) Go to CDN Metrics Page to see your requests (it may take 30 minutes for cybersecurecdn to provide initial metrics)
How do I schedule a malware scan?
To schedule malware scan:
1) Login to the Comodo cWatch Web Security
2) Click Register New Domain
3) Click domain name on left menu
4) Click Settings
5) Click Scan Settings
6) Click Download the php scan file
7) Connect to your File Manager and go to Web Root (usually public_html/www) (On Hosting)
8) Place downloaded php scan file to Web Root
Sample file manager scan file placed on cPanel (On Hosting)
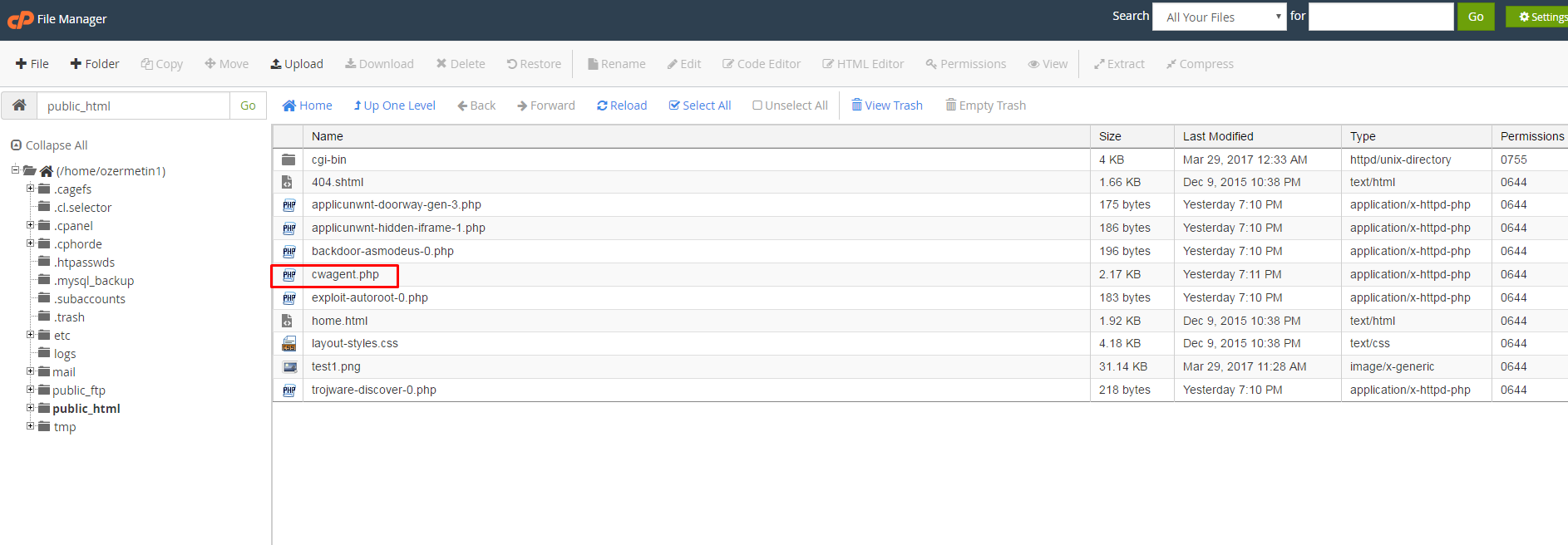
9) Copy the file path where the downloaded php scan file placed (On Hosting)
10) Paste file path to We will try to access the file at:
11) Click Save
How do I configure FTP settings?
To configure FTP settings
1) Login to the Comodo cWatch Web Security
2) Click Register New Domain
3) Click domain name on left menu
4) Click Settings
5) Click FTP Settings
6) Enter Host
7) Enter Username and Password
8) Enter Path and Port
9) Click Save FTP Settings
How do I configure SSL settings?
To configure SSL settings
1) Login to the Comodo cWatch Web Security
2) Click Register New Domain
3) Click domain name on left menu
4) Click Settings
5) Click SSL Settings
6) Enter your crt (certificate) between -BEGIN CERTIFICATE- / -END CERTIFICATE-
7) Enter your key (certificate) to -BEGIN PRIVATE KEY- / -END PRIVATE KEY-
8) Click Create New SSL Certificate (SSL Chain Certificate is optional)
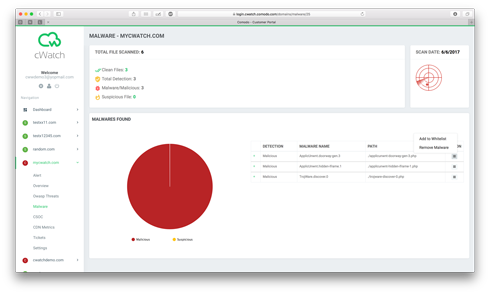
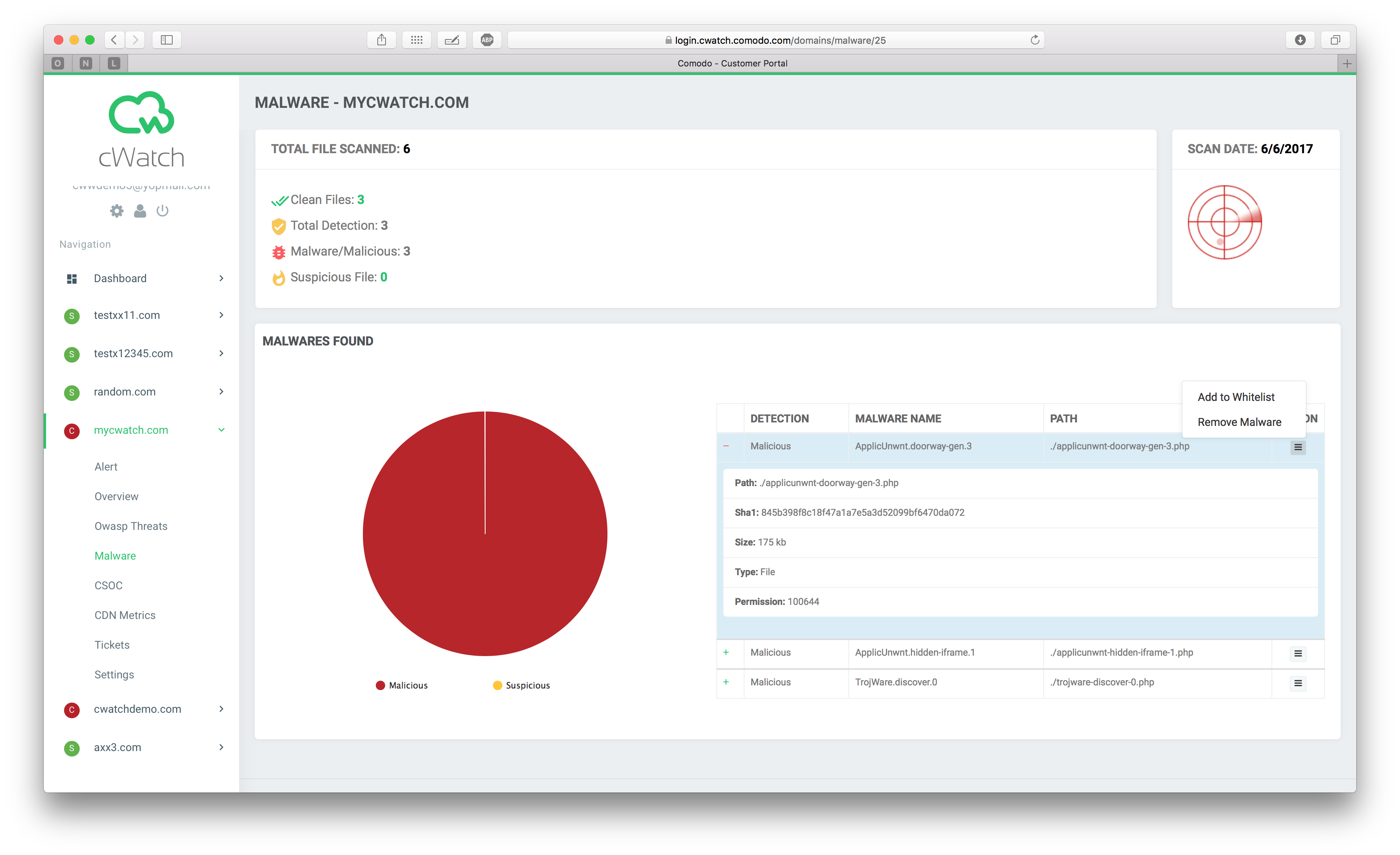
I have a malware on my site, how do I remove it?
To remove malware from your site:
1) Login to the Comodo cWatch Web Security
2) Click domain name on left menu
3) Click Malware
4) See Malwares Found and click on Action
5) Select Remove Malware action
6) Add your description (if needed)
7) Click Add (you can click see details to see your ticket)
How do I edit my profile?
To edit your profile:
1) Login to the Comodo cWatch Web Security
2) Click human icon (between Settings and Logout buttons)
3) Click Edit Profile
4) Edit your profile
5) Click Save
How long does it take for my site to be created on CyberSecureCDN?
New site creation on CDN takes around 15 minutes. So it may take up to 15 minutes before you see some metrics on CDN Metrics page.
Why do I enter FTP settings?
FTP settings are entered so that Cyber Security Operation Center experts may access your domain in order to analyze and remove malware.
How do you verify domain ownership?
For Malware Scan, CNAME Settings and FTP settings, you must have credentials for your domain or file manager. If you have access to these, you are the owner of the domain.
What is the malware schedule period?
Malware schedule period is the time that you schedule a malware scan. After the first scan, a malware scan occurs at that same time each day.
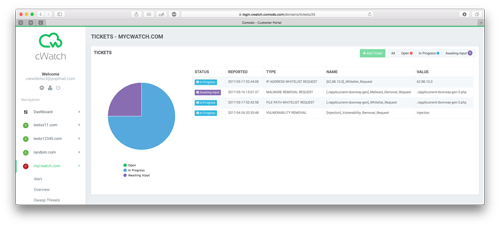
How can I communicate with CSOC operators?
You may communicate with Cyber Security Operations Center experts by creating a ticket.
Remove malware from any website. Guaranteed.
What happens when your website has been hacked? The malware may be hidden, difficult to detect and your website may be the unwitting point for creating other infections. In many ways, these scenarios mimic the real world of infections. What is at risk?
The answer is everything including the reputation of your business – the trust that is why your clients do business with you may take serious damage. By the time you learn of this problem, the damage may be done. Now you're worried about the cost and time it's going to take to clean this up – how to recover your website and the reputation of your business. That's when you need help from people you can count on. Comodo can help on the prevention side (where it is best applied) and on the mitigation when the damage is done and you need professional help.
Get peace of mind with our cWatch Website managed security services. cWatch is the platform of tools and expert services to put world class prevention in place and assist with the mitigation to get your website clear of the malware and available to your clients. You likely came to know of us via word-of-mouth recommendations. There is a reason for that. It's because we fix hacked sites faster and better than you can imagine, and we cut through noise others depend on. We are thorough, efficient, and we care about making your website safe.
Comodo is familiar with many attacks
- Any Hosting Provider
- Blackhat SEO SPAM Injections
- Malicious Redirects
- Dirty Search Engine Results
- Hidden & Malicious iFrames
- Redirections Targeting Mobile Devices
- Any CMS or Custom Setup
- Unlimited Pages
- Phishing Lures
- Hijacked Websites
- Obfuscated JavaScript Injections
- Redirections Targeting Mobile Devices
- Drive-by-Download Injections
- Email SPAM Abuse
- Pharma Hacks
- Desktop AntiVirus Blacklisting
- Infected Database / SQL Injections
- Website Defacements
- Embedded Trojans
- Cross-Site Scripting (XSS) Infections
- Search Engine Blacklisting (Google, Bing, Yahoo, etc)
What to expect during website malware removal
Comodo's Cyber Security Operations Center (CSOC) offers 24/7 service to analyze your website for malicious content and eliminates threats. Our technology combines automatic scans with in-depth human reviews, so that we review every bit of information from your websites. We keep track of changes and alerts are generated accordingly for modifications to content. Comodo's CSOC also monitors third-party blacklists and blacklist engines so that we will get know before anybody else to work for you regarding malware removal and blacklist removed. Comodo AVTeam and Research Lab uses all information gathered around the world to keep our tools and techniques up-to-date. So that we will be ready for emerging threats and zero-day malwares.
The cleanup is conducted remotely using FTP. Our analyst will create backups of all modified or removed files and remove or patch the content only as needed. You will get extensive report about what has been fixed and also will get all original files. Once the website is clean, we submit a review with third-party blacklists, and the appropriate blacklist engines to crawl your website. While Comodo cannot control the pace at which these entities operate, we do have the advantage of our brand, our relationships, and the volume of submissions on a daily basis.
Correlating all of the information, we will direct you to the main cause and help you to remediate the main cause to be sure that it won't occur again. With our guidance you will be able to harden your website after the cleanup to prevent future attacks. You will also be able to enroll for our continuously monitoring & protection services that is served by our Security Operation Center 24/7. So we are sure that it will not happen again.
At Comodo, we believe that investing time, effort, and resources into research and remediation is the only way to build a strong website security company. Our systems and approach are built from years of experience and revolve around three key elements - People. Process. Technology.
Compromised Indicators
- Google, Yahoo, Bing have blacklisted your website
- Visitors say your website is flagged by their Anti-Virus
- Your host has disabled your website for security
- Google is showing spam in search results for your site.
- You are plagued with reinfections
- "This site may be compromised" warnings on Google
- Visitors get redirects on mobile devices
- Strange website behavior or downloads popping up